Streamline workflows, reduce IT costs and optimise your content by keeping it up-to-date and performing in real-time.
What differentiates us from the rest of the market is the unique solution.
With THRON PLATFORM you no longer have to deal with different software and integration costs.


Cut licensing and integration costs of different tools. No wasted IT budget to integrate and maintain different tools.
With the unified taxonomy, AI-powered engines, and asset-product associations, you can quickly access everything you, your partners and customers need.
Data and media are AI-optimised, published everywhere, updated in real-time and at peak performance.
Each area of THRON PLATFORM works in synergy to optimise every stage of your media content and product information lifecycle, from management to distribution.



Thron PLATFORM
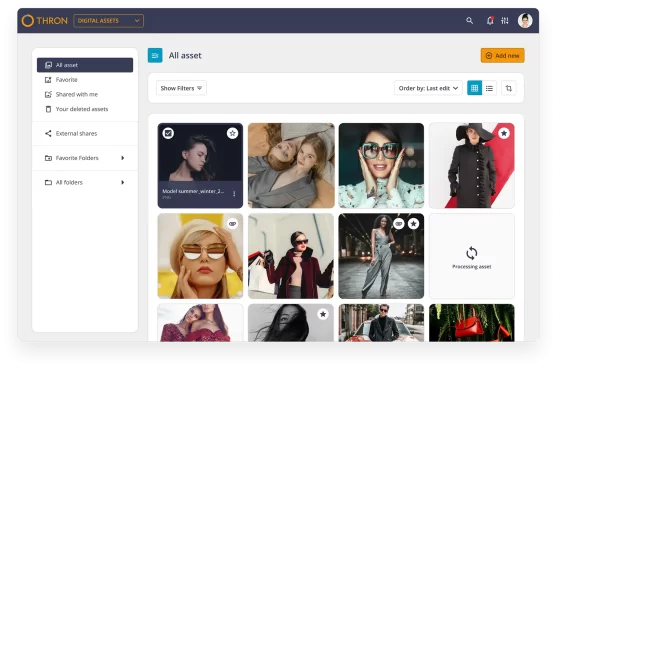
Organise all your digital assets in any format and instantly find what you need.
Boost your media content’s creative and approval flows with our natively SaaS DAM software.



Thron PLATFORM
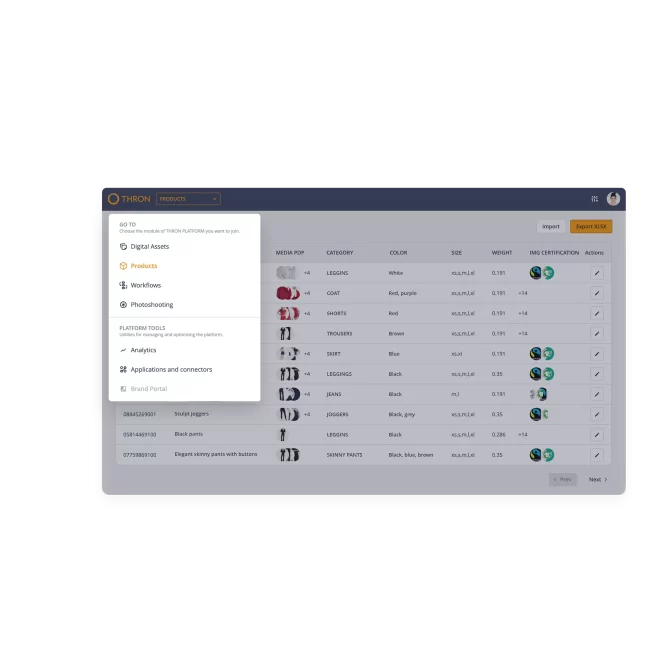
Product Information and Digital Media travel on one platform, giving you unprecedented ease and speed.
Manage variants in real-time and generate engaging multilingual descriptions for your product sheets automatically, thanks to AI.
Everyone’s work for everyone’s benefit.
Thron PLATFORM
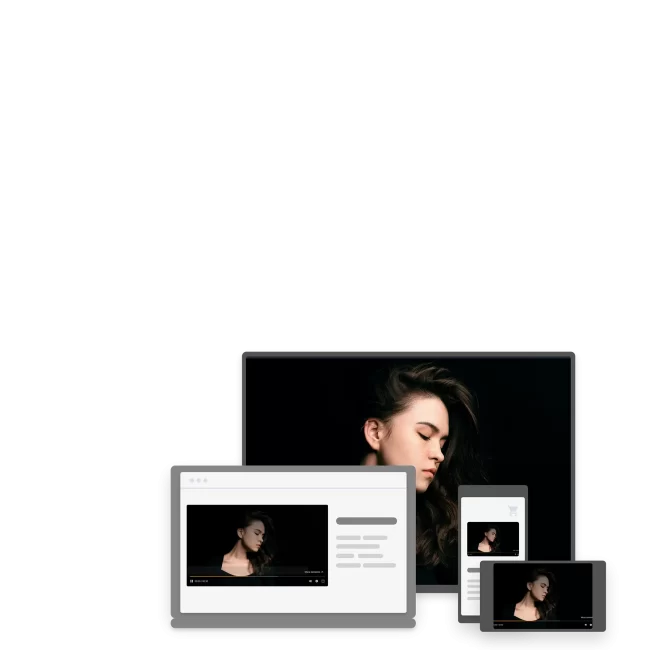
Boost your performance on every touchpoint.
Publish, retrieve, and update content directly from the DAM, optimising it in real time for websites, e-commerce, and marketplaces.
Ensure your users enjoy an optimal browsing experience in any context. The AI intelligently balances loading speed and visual quality, automatically selecting your content’s ideal format and resolution.
Teams collaborate effortlessly and fluidly, instantly leveraging each other’s contributions without barriers.
Massively import all your content and product data.
Let creativity fly with connectors for your graphics suites.
Turn management into governance, say goodbye to duplicate data and assets.
Always find what you need, classify and categorise on the fly with AI.
Approve, review, comment and exchange feedback in an agile way.
Design any digital workflow without writing code.
Publish assets and data automatically and in real time on every channel.
Make the voice of your brands consistent across any touchpoint.
Power is important, yes, but never give up control.
Analyse volumes, performance and access to every assets and data.

SUCCESS CASE
THRON is SaaS and cloud-native platform. Its flexible architecture and technology guarantee consistently high performance, regardless of traffic load.
THRON AI is the artificial intelligence that automates and handles all tasks related to content and products typically done manually. It streamlines your workflow and boosts productivity.

With a unified data structure for DAM and PIM, any team its always on the same page, minimizing the risk of errors or miscommunication across departments, systems, and channels..

Access to the platform is fast, automated, and secure. From a single control centre, you can manage the access rights of users and user groups.
THRON collects performance data for you, enabling data-driven strategies to optimise your information assets management.

Share or revoke assets across channels, apps, and users instantly. Real-Time Content Access automatically verifies permissions, providing easy and secure control.

Your content and data are always available, protected and intact.
THRON is an AWS Partner and certified
ISO 27001:2022, ISO 27018:2014 e ISO 9001:20015.

THRON’s APIs are modern, powerful and easy to implement.
Native connectors allow you to reach any web channel in moments.

With 100% positive feedback, the Customer Service team is one of our prides.
Together with the Success Managers, they help customers maximise THRON’s potential.


These are the annual hours of manual labour recovered with THRON by a company with 1,000 product codes and an average of three pieces of content, each to be published on three web channels.
Find out how many hours you can recover with THRON and over 10 customised KPIs for your company!
